When I bought a new notebook recently, I resolved to take better care of my laptop battery this time than I had with my previous ones. With my last laptops the battery was more or less dead after a year or so. If a battery is treated with care it can last up to four years. I thought that I knew how a notebook battery has to be handled, but after googling this topic , I realized that quite a few of my beliefs were outdated.

There are two important keywords when it comes to battery preservation:
Charging and Temperature.That is, how the batteries are charged, and the temperatures to which they are exposed, are key factors that determine their lifespan.
There is a lot of confusion surrounding this issue, mostly because lithium-ion batteries are different from older, Nickel-based batteries ,Charging them incorrectly can decrease their Lifespan.
Most lithium batteries should last you a few years, but improper care can decrease that lifespan, meaning that your battery will be unable to hold a charge or unable to hold as big a charge as it used to quicker.
So, to clear things up, here's how to actually extend your battery's health as much as possible.
- Don't leave it fully charged :
Lithium-ion batteries don't need to be charged all the way to 100%. In fact, they'd prefer not to be so the
40% - 80%rule you heard is a good guideline. When possible, keep it in that range to prolong its life as long as you can. And, if you do charge it to 100%, don't leave it plugged in. This is something most of us do, but it's
another thing that will degrade your battery's health.
- Perform shallow discharges :
Instead of discharging to 0% all the time, lithium-ion batteries do best when you discharge them for a little bit, then charge them for a little bit. The table from Battery University, shows that discharges to 50% are better for your battery's long-term life than (since the 50% discharges provide the best number of cycles-to-usage ratio).

Depth of discharge (DoD) determine the cycle count. The smaller the depth of discharge, the longer the battery will last.
Most people overlook this one. Excess heat is not only bad for your processor (and your lap), but your battery as well.

Once again, see the table from Battery University at the right side a hot battery will degrade in health much quicker than a cool one. As such, I highly recommend using a laptop stand or Cooling Pad.
- Fully discharge it once a month :
This may seem contradictory, but hear us out. While lithium-ion batteries shouldn't be discharged regularly, most modern batteries are what's known as "smart batteries", which means that they can tell you how long you have until your battery dies (e.g. "2 hours, 15 minutes remaining"). This feature can get miscalibrated
after a lot of shallow discharges. So, manufacturers recommend fully discharging your battery once a month to make sure this stays accurate.
Keep these things in mind and your battery will last longer.




















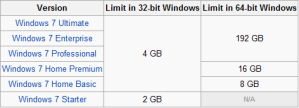
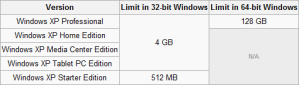
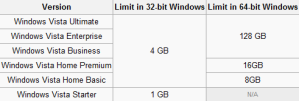
 icon in your Windows system tray
icon in your Windows system tray
















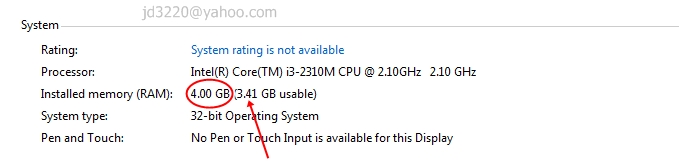
 While 32 bits of information can only access 4 GB of RAM, a 64-bit machine can access 17.2 BILLION gigabits of system memory, banishing any limits far into the future. This also means that your video cards and other devices will not be stealing usable memory space from the operating system.Windows 64-bit Home editions are still limited to 16 GB of RAM for licensing reasons, but the Professional and Ultimate versions can use up to 192 GB of RAM, so keep that in mind when building that killer system.
While 32 bits of information can only access 4 GB of RAM, a 64-bit machine can access 17.2 BILLION gigabits of system memory, banishing any limits far into the future. This also means that your video cards and other devices will not be stealing usable memory space from the operating system.Windows 64-bit Home editions are still limited to 16 GB of RAM for licensing reasons, but the Professional and Ultimate versions can use up to 192 GB of RAM, so keep that in mind when building that killer system.